As a developer working with Internet of Things (IoT) devices and ecosystems, you’re facing a rapidly evolving landscape of state, national, and international regulations. These rules are designed to ensure cybersecurity, and your challenge is threefold: you must identify all the regulations that apply to your IoT products, interpret what they require, and implement effective strategies that are recognised by both regulators and the market.
This guide will help you navigate these challenges in the context of the European Union’s Cyber Resilience Act (CRA) and explain how independent third parties can validate your compliance efforts.
Understanding the Cyber Resilience Act
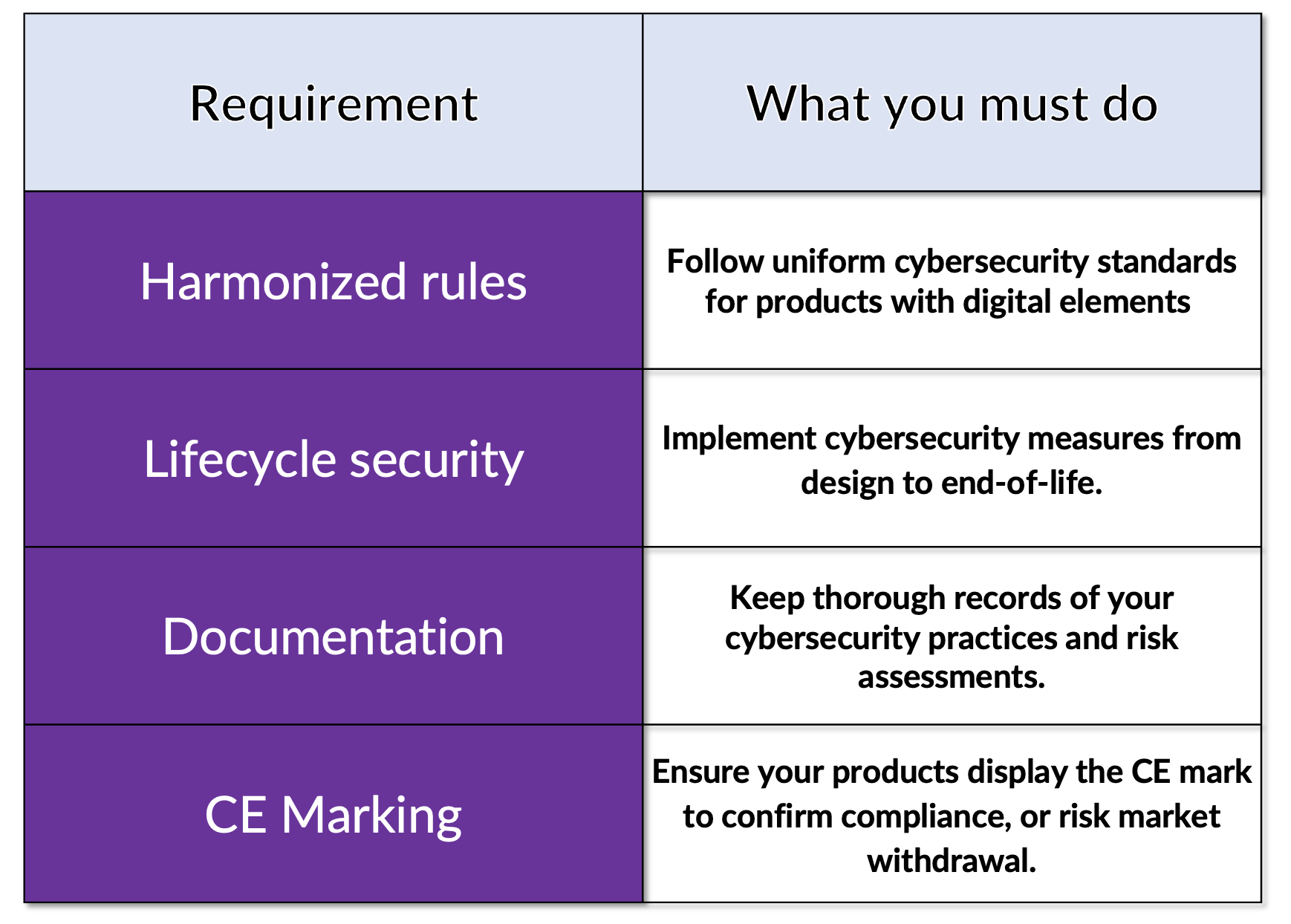
When you develop digital products or services that connect to other devices or networks, the CRA mandates that these must be secure by design, resilient against cyber threats, and protected throughout their entire lifecycle.
The CRA came into force on 10th December, 2024, and its implementation is staggered across three key phases:
- By 11th June, 2026, EU member states must submit the names of organisations within their jurisdiction that intend to offer CRA conformity assessments
- By 11th September, 2026, you must be able to report actively exploited vulnerabilities and severe incidents
- By 11th December, 2027, all other CRA requirements become mandatory
These deadlines may seem distant, but preparing for them is essential if you want to avoid last-minute challenges. You’ll find that many technical requirements are as expected: you need to adopt cybersecurity-by-design strategies, provide secure-by-default configurations, and implement robust encryption and access controls.
However, the Act also requires you to:
- Conduct and regularly update risk assessments
- Address vulnerabilities throughout your product’s life
- Exercise due diligence when integrating third-party components or services
- Maintain comprehensive documentation, including a declaration of conformity
Here’s a summary of what you need to address:
Failing to comply can result in significant penalties, including fines up to 2.5% of your global annual turnover, sales restrictions, or even product recalls.
Tackling compliance challenges
To effectively address the CRA’s requirements, you can use structured tools that help you analyse what the Act demands and how to adjust your design processes accordingly. These tools can also reveal areas where your efforts alone may not suffice – such as when your product’s cybersecurity depends on an external service.
Independent third-party assessments are invaluable for demonstrating to regulators and the market that you’ve met the CRA’s requirements. These assessments must be impartial to be credible.
One example is cetome, a global security consultancy. cetome helps you protect your products and services against known cyber risks, respond to emerging threats, and stay abreast of evolving cybersecurity legislation. Its independent advice and compliance assessments are crucial for building trust in your IoT devices and systems.
How Cetome assessed Quarklink
Consider how Crypto Quantique, a company specialising in software and semiconductor intellectual property, approached CRA compliance. It offers end-to-end IoT security technologies, from chip-level security to software tools that automate secure device onboarding.
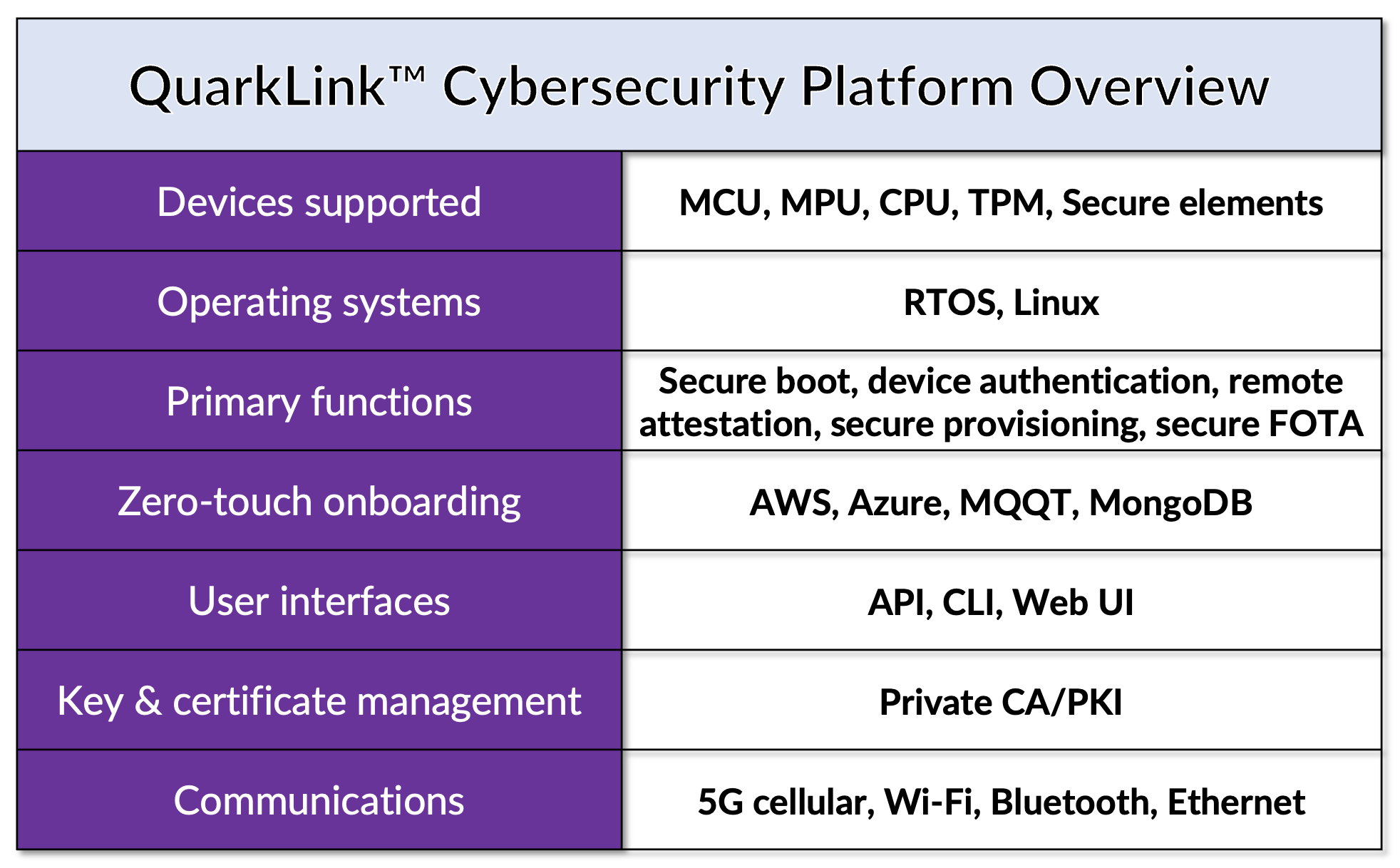
Its QuarkLink software platform simplifies security-by-design by managing on-device key generation, certificate management, secure boot, and flash encryption. It supports a range of Linux distributions and hardware, and RTOS running on microcontrollers or powerful SoCs.
Crypto Quantique engaged cybersecurity advisory firm cetome to independently evaluate how well QuarkLink helps customers meet CRA requirements when developing IoT products and services.
QuarkLink consists of two main components:
- The QuarkLink Software Development Kit (SDK), which enables secure boot and manages secrets and certificates on devices
- A Cloud platform for secure device provisioning, onboarding to thirdparty Cloud services, and key management
cetome’s assessment, conducted in early 2025, mapped QuarkLink’s features against each Essential Cybersecurity Requirement in Annex 1 of the CRA. For each requirement, cetome rated QuarkLink’s support as:
Excellent: you can achieve compliance with minimal extra effort
Good: the platform helps, but you may need to do some additional work
Fair: compliance is possible, but only if you meet certain prerequisites
If you see a ‘Good’ or ‘Fair’ rating, it often means that some compliance work falls outside the scope of what a software platform like QuarkLink can provide.
A PDF copy of the report is available here.
Interpreting technical requirements can be tricky. For instance, while the CRA doesn’t explicitly require secure boot for embedded IoT devices, it does require you to address vulnerabilities within 48 hours. Often, this means issuing over-the-air firmware updates – something you can only do securely with a hardware root-of-trust and secure boot mechanisms.
cetome’s report concluded that QuarkLink “offers a comprehensive all-in-one solution to create and operate secure-by-design products.” The platform simplifies complex hardware-based security functions by abstracting them through the SDK, and Crypto Quantique’s partnerships with chip vendors further streamline implementation.
QuarkLink also excels at managing security secrets and certificates throughout a product’s lifecycle, reducing risks like insecure cryptography, misconfiguration, leaked secrets, and expired certificates. However, cetome cautions: “With QuarkLink, product manufacturers can accelerate their compliance with several Essential Requirements of the CRA. QuarkLink is only an enabler to product security: you still need to follow
a secure-by-design process and apply the CRA Essential Requirements across your entire product, including mobile applications and Cloud services.”
This independent assessment makes it clear how tools like QuarkLink can support your CRA compliance efforts, while also highlighting what additional steps you must take.
Moving forward
Regulations like the CRA are becoming a global reality, and you can’t afford to ignore them. Some requirements are highly specific and must be understood, implemented, and validated – both in the marketplace and by independent assessment bodies – before you can be sure your designs are compliant.
Platforms like Crypto Quantique’s QuarkLink can help you think through and implement solutions that meet regulatory demands. At the same time, independent consultants such as cetome can help you – and the wider market – understand how well you’re meeting the CRA and other emerging regulations in practice.
David Haslam, Head of Software Engineering, Crypto Quantique
This article originally appeared in the July/August issue of Procurement Pro.